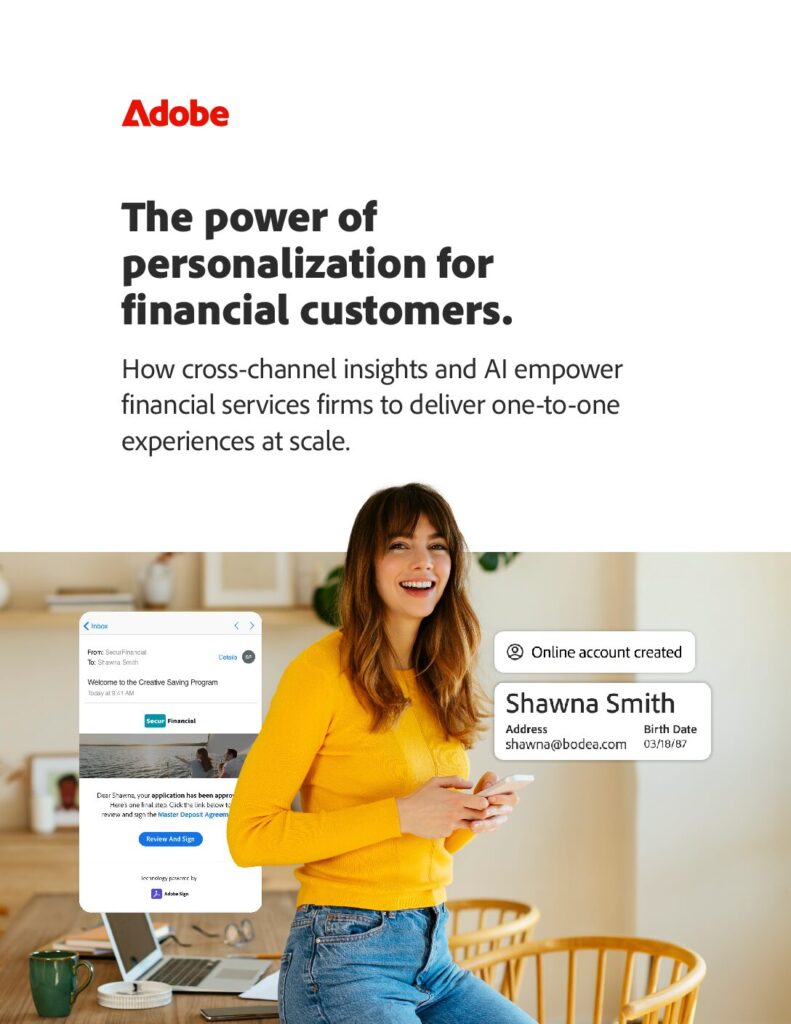
The power of personalisation for financial customers
The power of personalisation for financial customers It’s likely that your financial organisation possesses the data necessary to deliver seamless, cross-channel interactions and customised engagements for customers — but transforming that data safely and responsibly into actionable insights remains a significant challenge. Check out the Power of Personalisation for Financial Customers guide for strategies and […]
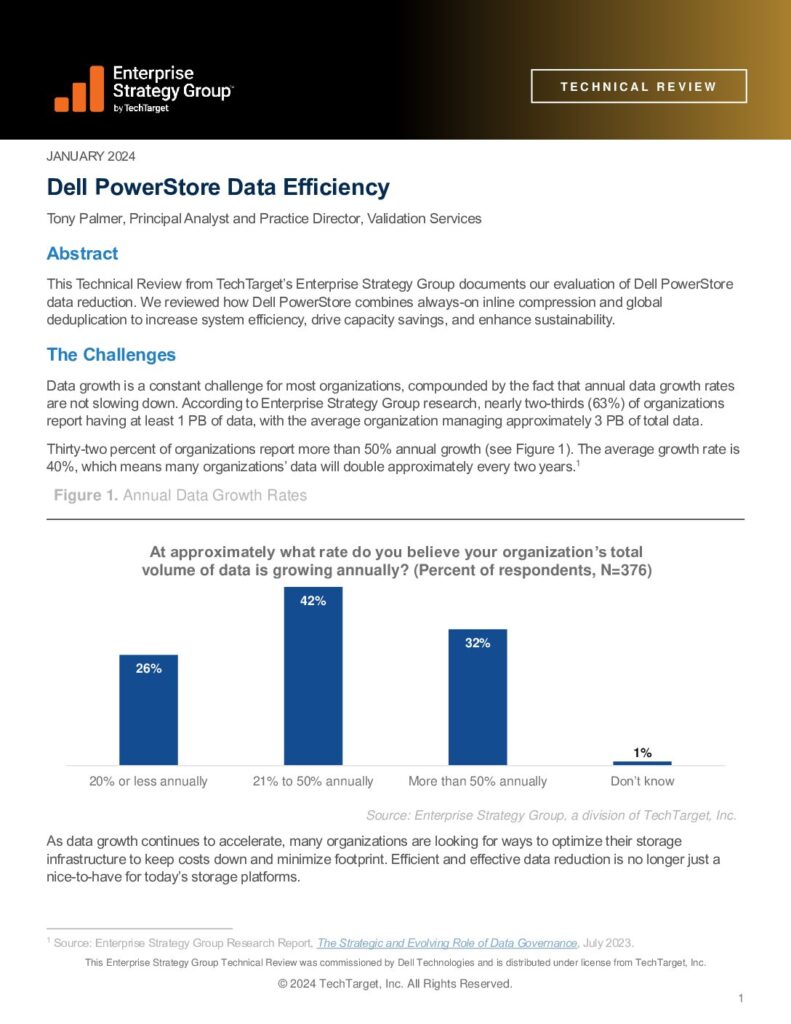
The power of personalisation for financial customers Read More »